KMS Multi-Accounts
Once the custom KMS Keys has been enabled from: Config > Settings > Amazon Web Services
Enable Multi-Domains from: Configuration > Settings > Active Directory and tick on “Multiple Domains”

The KMS Keys will now display for the same account in which the WSM is deployed:

In a multi-accounts scenario in AWS, you need to change the policies attached to the role in the secondary (or more) accounts and specify to WSM which role to use in each case. This is done in two different places: 1) In the secondary account in which you assign permissions for KMS to the existing role. 2) In WSM, for each account with WorkSpaces that are monitored, the role to assume has to be explicitly specified.
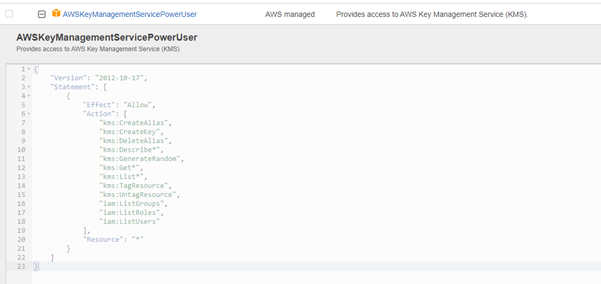
In the secondary account (and more if needed), a role like arn:aws:iam::222222222222:role/AllowWSMAccess will be edited and an AWS Managed Policy called “AWSKeyManagementServicePowerUser” will be added:
In WSM, you need to add the role that you are to use from a different account:
Last updated

